
August 22, 2023
Data Security Platform: Securing the Digital Perimeter
Anil Bhat
Senior Vice President Technology & Engineering
In today’s data-driven world, organizations face increasing challenges in protecting sensitive information while ensuring compliance with stringent data privacy regulations. The exponential growth of data has also led to a higher risk of unauthorized access, breaches and cyber-attacks being faced by organizations. In such a scenario, protecting sensitive information is a top priority for businesses, and the use of Data Security Platforms (DSP) has emerged as a crucial component in the battle against data threats. This article delves into the significance of a DSP, its role in compliance with data privacy regulations, and the common challenges faced during adoption.
What is a Data Security Platform?
A Data Security Platform is designed to protect sensitive and valuable data from unauthorized access, breaches and other security threats. Gartner defines Data Security Platforms (DSPs) as products and services characterized by data security offerings that target the integration of the unique protection requirements of data across data types, storage silos and ecosystems.
Gartner, in their report “2023 Strategic Roadmap for Data Security Platform Adoption” lists 6 capabilities required for a Data Security Platform (Fig 1)
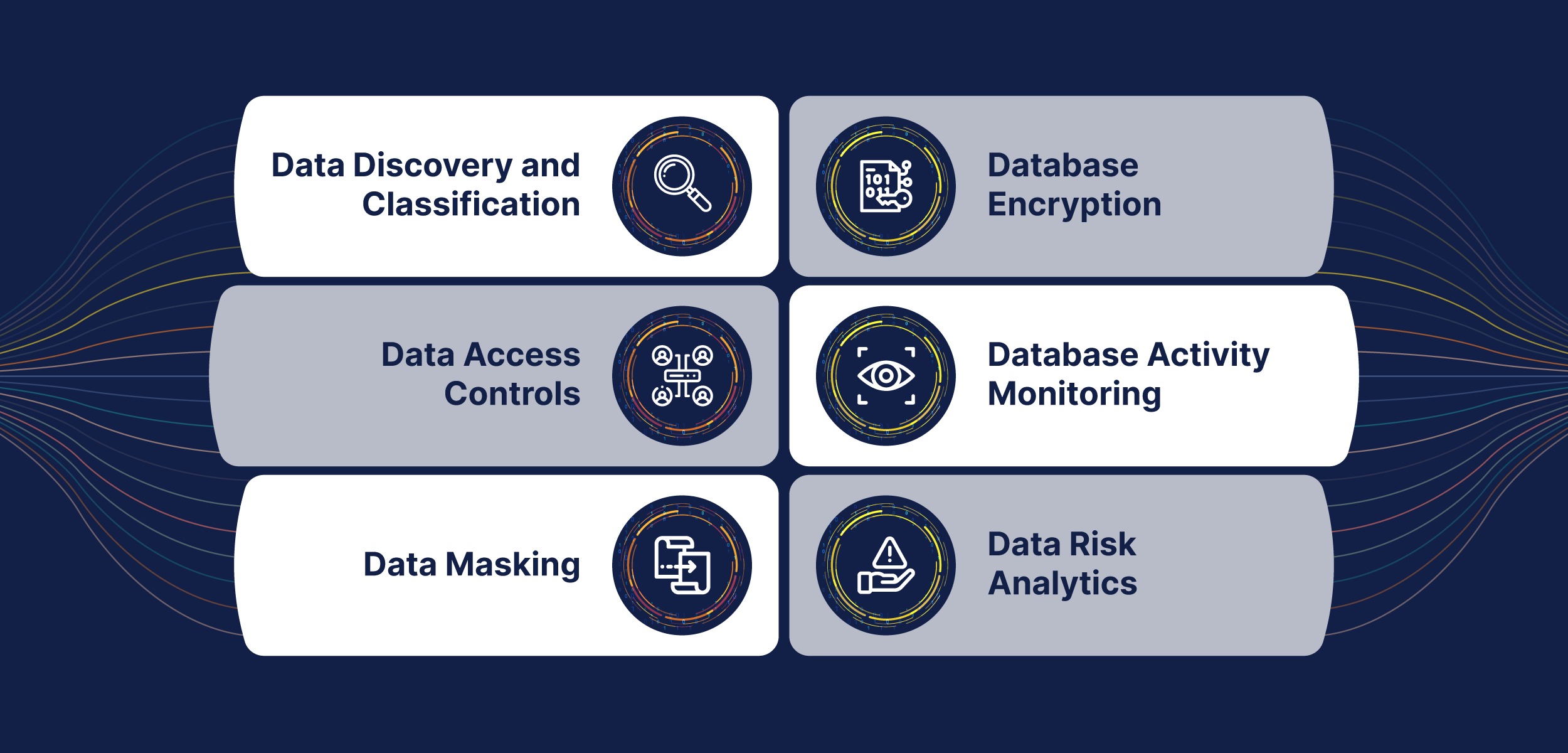
Fig.1
Let us go through each of these capabilities in detail:
Data Discovery and Classification
Data Discovery and Classification involves the automated scanning and analysis of an organization’s data repositories to identify and categorize sensitive data. This process helps organizations understand where sensitive information resides, such as personal identifiable information (PII), financial data, intellectual property, or other confidential data.
The data classification process tags data with relevant labels indicating its sensitivity level and compliance requirements. For example, data might be classified as “Confidential,” “Internal Use Only,” or “Public.” This classification enables organizations to enforce appropriate access controls, data protection measures, and data handling policies based on the data’s sensitivity. It also aids in compliance with data protection regulations since organizations can ensure that sensitive data is treated according to the applicable laws.
Data Access Controls
Data Access Controls are mechanisms that ensure only authorized users have appropriate access to specific data. This component plays a vital role in preventing unauthorized access to sensitive information, reducing the risk of data breaches and insider threats.
Role-based access control (RBAC) is a common approach in data security platforms, where permissions are assigned based on the user’s role within the organization. Access rights can be granted or revoked based on job functions, ensuring that users only have access to data they need to perform their tasks.
Data Access Controls work hand-in-hand with the data classification process, as the access privileges are often determined based on the sensitivity level of the data. Strong access controls help ensure that data is only accessible to authorized individuals and minimize the risk of data leaks or unauthorized disclosures.
Data Masking
Data Masking is the process of concealing original sensitive data by replacing it with realistic but fictional data. The purpose of data masking is to create a structurally similar version of the data without revealing the actual information. This is particularly important for non-production environments like testing or development, where real data is not needed.
Data Masking is commonly used to protect sensitive data while ensuring that applications and processes can still function realistically with representative data. This prevents the exposure of actual sensitive data during testing or other non-production activities, reducing the risk of data breaches resulting from mishandling or accidental leaks in lower-security environments.
Database Encryption
Database Encryption involves converting plaintext data into ciphertext using encryption algorithms, rendering the data unreadable and useless without the appropriate decryption key.
At-rest encryption ensures that data stored on disk or in a database is protected even if physical storage media is compromised. In contrast, in transit encryption safeguards data as it is transmitted over networks, preventing eavesdropping or interception by unauthorized parties.
Database encryption adds an extra layer of security, making it significantly harder for attackers to access sensitive data, even if they gain unauthorized access to the underlying infrastructure.
Database Activity Monitoring
Database Activity Monitoring (DAM) is a real-time surveillance mechanism that captures and records user activities and behaviors related to database access and usage. It tracks queries, data modifications, login attempts, and other interactions with the database.
DAM helps detect suspicious or unauthorized activities, such as unauthorized attempts to access sensitive data or unusual data access patterns. When abnormal behavior is detected, the system can trigger alerts to security teams, enabling them to respond promptly to potential security threats and prevent data breaches.
Data Risk Analytics
Data Risk Analytics involves the use of advanced analytics and machine learning techniques to assess security risks associated with an organization’s data environment. By analyzing patterns, trends, and historical data, this component can identify potential vulnerabilities and predict security risks before they escalate.
Data Risk Analytics helps security teams gain insights into potential data security issues, such as weak access controls, suspicious user behaviors, or unsecured data repositories. These insights enable organizations to take proactive measures to strengthen their overall data security posture and mitigate potential risks before they lead to security incidents or data breaches.
The Advantages of a Data Security Platform (DSP)
In an era where data breaches and privacy concerns dominate headlines, organizations need to fortify their data security measures across the entire enterprise data landscape to safeguard their reputation, build customer trust, and sustain financial stability. A Data Security Platform (DSP) provides a centralized approach to data security, enabling businesses to efficiently manage data protection across various systems and applications. It serves as a comprehensive solution that comprises various components enabling data security across the sensitive data lifecycle. . By adopting a DSP, organizations can:

Figure 2
Ensuring Compliance with Data Privacy Regulations
The implementation of a DSP significantly aids organizations in complying with various data privacy regulations:
GDPR Compliance
The GDPR mandates stringent data protection measures, including data minimization, purpose limitation, and user consent management. A DSP helps organizations meet these requirements by implementing encryption, access controls, and consent management mechanisms.
CCPA and Other Privacy Regulations
The California Consumer Privacy Act (CCPA) and similar regulations empower individuals with greater control over their personal information. A DSP enables organizations to manage user preferences, handle data subject requests, and maintain auditable records for compliance.
Emerging Regulations
As new privacy regulations continue to emerge globally, a DSP provides a future-proof solution by offering flexibility and scalability to adapt to evolving compliance requirements. This ensures organizations can stay ahead of the regulatory curve.
Overcoming Challenges during DSP Adoption
While adopting a DSP offers significant advantages, organizations may face certain challenges:
Integration Complexity
Integrating a DSP with existing IT infrastructure and applications can be complex. To overcome this challenge, organizations should carefully plan the integration process, seek vendor support, and collaborate closely with IT teams to ensure a seamless deployment.
Employee Training and Awareness
The successful adoption of a DSP depends on the knowledge and awareness of employees. Organizations should invest in comprehensive training programs to educate employees about the DSP’s functionalities, data protection best practices, and the importance of compliance.
Balancing Security and Usability
Organizations may face the challenge of balancing data security measures with usability and productivity. It is crucial to strike the right balance by implementing security controls that protect data without hindering operational efficiency.
Keeping Pace with Changing Regulations
Data privacy regulations continue to evolve, necessitating ongoing monitoring and updates to the DSP. Organizations should stay informed about regulatory changes, actively engage with legal and compliance experts, and collaborate with the DSP vendor to ensure the platform remains up to date.
Conclusion
In an era where data security and compliance with privacy regulations are critical, a Data Security Platform (DSP) emerges as a comprehensive solution for organizations. By adopting a DSP, organizations can fortify their data security measures, ensure compliance with regulations, and mitigate the risks associated with data breaches. Although challenges may arise during adoption, proactive planning, employee training, and ongoing monitoring can help organizations overcome them and achieve data security excellence in today’s complex digital landscape.
At Mage Data, we focus our efforts on empowering organizations with the tools and technologies to secure their data throughout its lifecycle – from creation and storage to processing and transmission. With Mage, you get access to a Data Security Platform that has been ranked as the Gartner Peer Insights Customer’s Choice for 3 years in a row and has also been named as an Overall Leader for Data Security Platforms by KuppingerCole. If you’re on the lookout for a comprehensive Data Security Platform that meets your organization’s IT strategic goals, feel free to reach out.

